Are you recovering from a cyber attack? Most hackers will leave a backdoor on your website. A backdoor is a way for the hacker to get back inside of your website. They are hard to locate because they can be left almost anywhere. The backdoor will consist of a few lines of code that the hacker can use to get inside of your website.
Every website is different and the same can be said for the hackers who leave them. Unfortunately, there is not just one place where a hacker will leave a backdoor. This makes it very hard to locate one, especially when your not sure what you are looking for. Today, I will demonstrate where backdoors are commonly stored and what to look for.
Will There Always Be a Backdoor
It is always easy to assume the worst, but not every hacker will leave a backdoor. Just because hackers are skilled enough to break in does not mean they know how to leave a backdoor. With that said, it is still a likely possibility and every web developer needs to check for one after an attack. There are also different kinds of backdoors.
The most well-known backdoor consists of leaving code that can create new admin accounts. Admin accounts have complete freedom on a website and are very powerful. This is very dangerous in the hands of hackers. The less well-known are the remote-controlled backdoors. A hacker will leave lines of code that allow them to directly execute PHP code that they create. Both are quite serious and can be prevented by checking your website.
How to Locate and Fix a Backdoor on a Hacked WordPress Website
Today, I will demonstrate where backdoors are commonly stored and what to look for. Keep in mind that this is where they are commonly stored. There is still the possibility that a backdoor exists elsewhere. You will need access to your website’s cPanel, which is provided to you with your web hosting plans when you create an account. The first step is to search your website and the next is to delete the backdoor if you find one.
Websites are complex and are made up of a lot of different files working together. Since you will be exploring the back end of your website, you should take the time to create a backup. It is possible that you can make a mistake and delete or remove the wrong file. The backup will ensure you can correct any mistakes. Just make sure to update the backup if you do find a backdoor so it is not in your backup. Here are the most likely places a backdoor will be located.
Themes
Themes are present on every WordPress website which makes them very easy targets for experienced hackers to leave a backdoor on. The misleading part is that hackers will not target your active theme. Web developers will commonly go into their theme’s files to edit code and add new features and design choices. Instead, hackers will choose to leave a backdoor on your inactive themes. If your website is hacked, you should delete your inactive themes. You can, of course, reinstall them at any time if you find yourself in need of them.
Start by logging into the cPanel and clicking on the File Manager option. The File Manager will allow you to access all of the files related to your website.
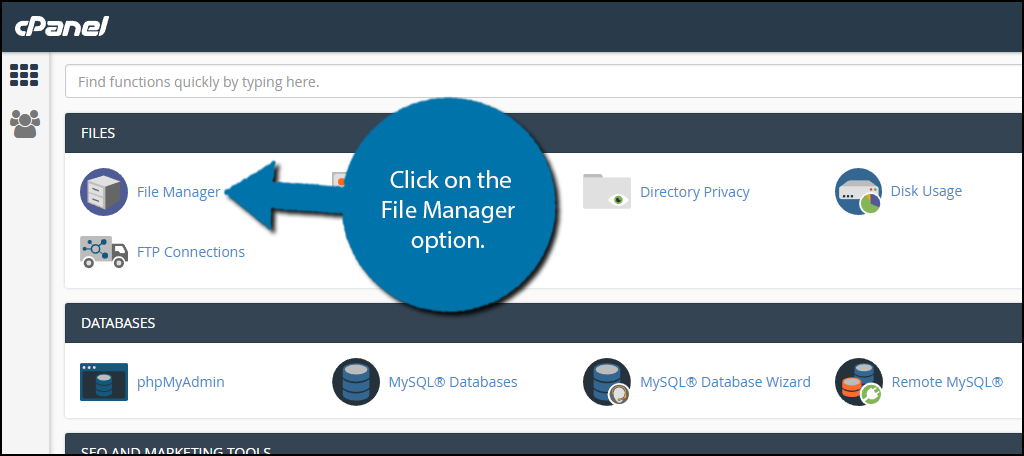
You need to locate your themes folders. Click on the public_html directory, then click on the wp-content folder. Inside of this folder, you will find all of the content related to your website. Click on the themes folder. You will see all of the themes you have installed on your website. Right-click on every theme you are not currently using and delete them.
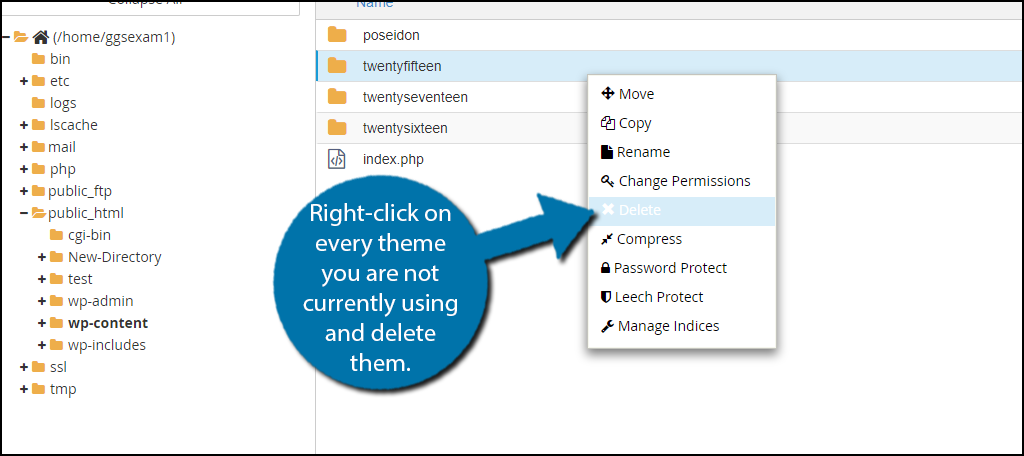
Feel free to install them again if you feel like you need them. This should not impact your website. Of course, it is still entirely possible that a hacker left a backdoor in your active theme. You need to carefully go through and look for recent additions. You may find an out of place file, which could be a backdoor in disguise.
Plugins
Plugins are just as common as themes and there are thousands to choose from. Some websites also keep a large number of plugins active and inactive. Like with themes, hackers will be more likely to target an inactive plugin. Unlike themes, it is not common for web developers to look inside of a plugin’s folder. This means that web developers do not know what the files should actually look like. As with themes, the solution is simple, just delete them. If they are not being used, there is no reason to keep them.
On the left-hand admin panel, click on the Plugins option. You will see all of your currently installed plugins. Click on the “Delete” option on your inactive plugins.
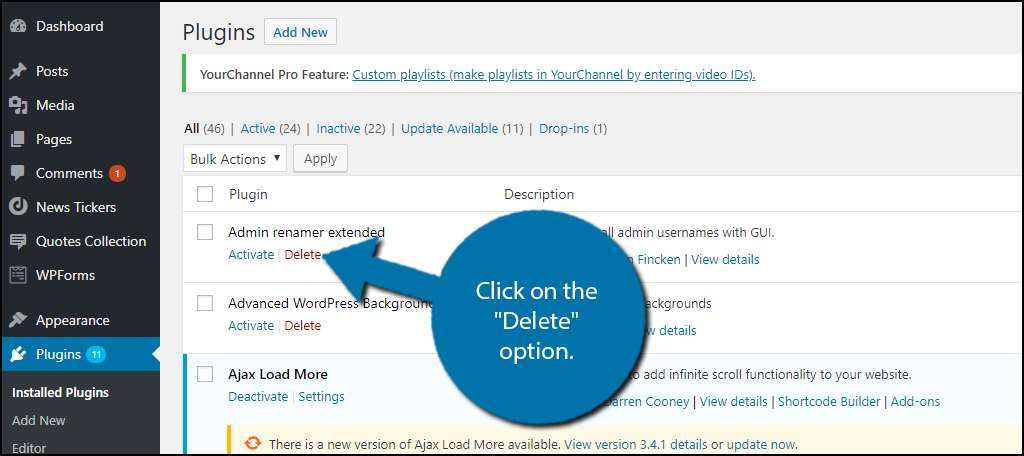
You can always install the plugin again if you need it. Now comes the not so easy part. You need to go to the plugins folder on your cPanel and go through the files for your plugins. You might have better luck deleting and installing a plugin again because it is very hard to identify what files are needed for the plugin.
Uploads
You will find yourself uploading media all the time as you create content for your website. Images, videos, GIFs, and all other content are uploaded as you need them. This is how almost every website does it and it’s extremely common, but when is the last time you checked your uploads? Probably you can’t remember, because that is not something web developers check, which makes it the perfect place to slip a backdoor in. It may be very easy to locate something that you never uploaded, but if you have multiple authors it becomes more complicated. If you are sure that you only upload one type of file, like images, then you can tell if something is not a certain file type.
Go to your cPanel and access the file manager. You need to locate your uploads folder. Click on the public_html directory, then click on the wp-content folder. Inside of this folder, you will find all of the content related to your website. Click on the uploads folder.
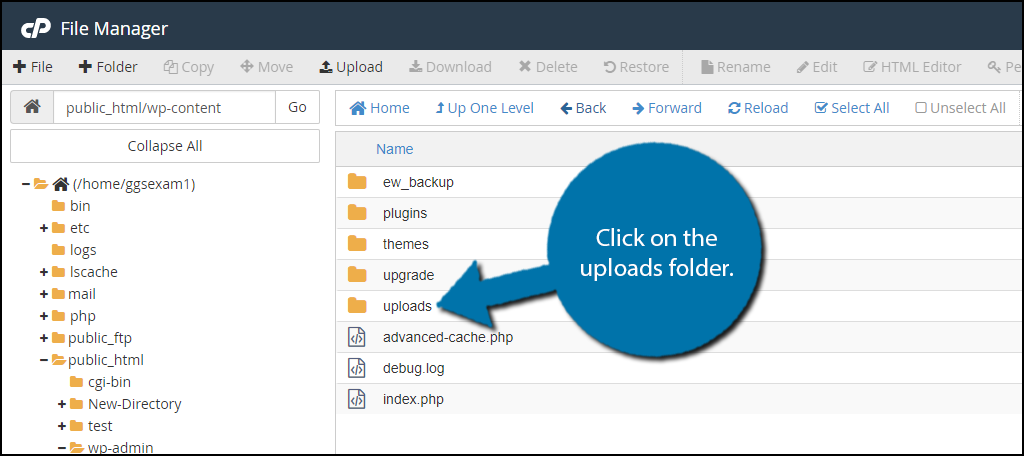
You will see multiple folders that separate your uploads by year (if your website is that old) and some uploads made by plugins. Check these files to be sure that everything is in order. If you don’t recognize an upload examine it and delete it if necessary.
wp-config.php
The wp-config.php file is located in the public_html directory. It is one of the most targeted files but is actually a poor choice. Almost all web developers are instructed to check this file after a hacking has taken place.
You need to locate and edit your wp-config.php file. Click on the public_html directory. Right-click on the wp-config.php file and select the Edit option.
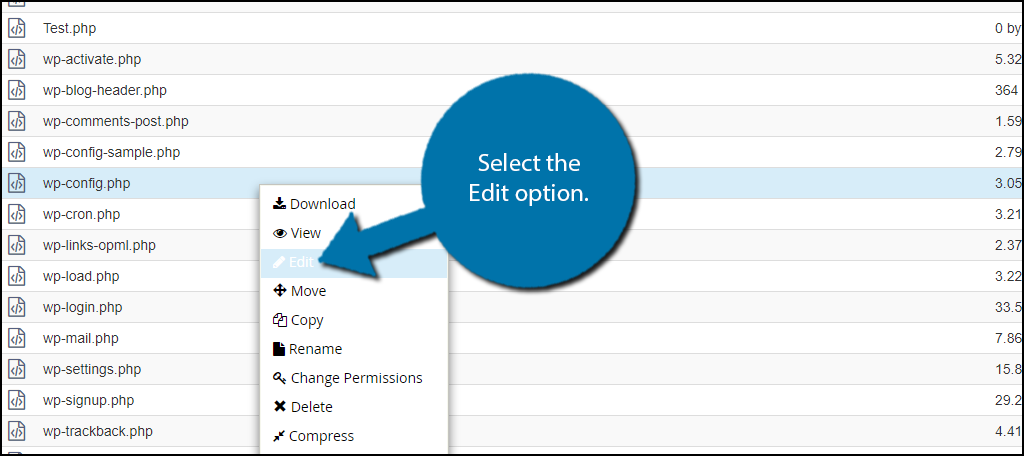
Go through the file very carefully and look for extra PHP code that does not belong there.
Is there Only One Backdoor
So you found the backdoor and deleted it, that’s great, but you’re not done yet. Hackers can leave multiple backdoors and that is why it is important to be thorough. Smarter hackers will leave an easily detectable backdoor. This way it is found by a web developer who then stops looking for others while the real backdoor is located elsewhere. It’s a common occurrence and can really throw novice web developers for a loop.
Guard Your Website
Hacking happens for many reasons and it is a painful experience for everyone. WordPress is a very well guarded platform with no vulnerabilities, as long as you are using the latest version. Unfortunately, hackers still find a way to get through. That’s why additional security plugins are a must to guard your website.
Have you located and repaired a backdoor on your website? How long has it taken you to search your website?

Good Post
Good Writting